Digital Security
Operations Services
IT HUB Digital Security Operations Center
The Digital Security Operations Center is the core of the IT HUB and serves as the operational hub for the entire digital security system. In this center, a professional team constantly monitors various network attacks and security vulnerabilities to ensure the secure and stable operation of the entire IT system. We have the most advanced security technology equipment and tools here, which can promptly detect and respond to any potential threats. Team members act like guardians, guarding the security of the entire digital world in the darkness. Their work requires a high sense of responsibility and technical ability, and every threat that arises can trigger a disaster. Their efforts make our online world more secure and reliable.
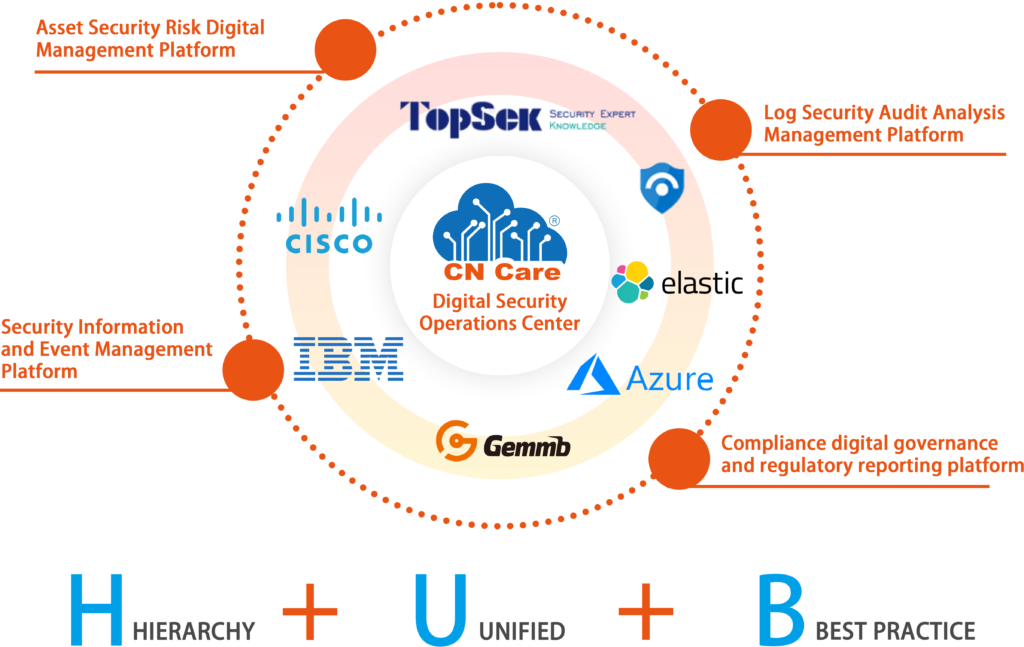
Security Service Catalog
Safe Transportation Services
– Security situation and weak password assessment.
– Security incident management and code leakage inspection.
– Security vulnerability management and security intelligence services.
– Security incident handling and security AI analysis services.
– Internet asset detection, software security version management.
– Open source software security management, security orchestration, and automation services.
– Security incident management and code leakage inspection.
– Security vulnerability management and security intelligence services.
– Security incident handling and security AI analysis services.
– Internet asset detection, software security version management.
– Open source software security management, security orchestration, and automation services.
SIEM Platform Services
– Asset Management
– Report Customization
– Event Alert
– Security Scenario
– Security Vulnerability Scanning
– Visual Dashboards
– Report Customization
– Event Alert
– Security Scenario
– Security Vulnerability Scanning
– Visual Dashboards
Security Log Service
– Log Query
– Report Customization
– Event Alert
– Security Scenario
– Visual Dashboards
– Centralized Collection and Storage Of Logs
– Report Customization
– Event Alert
– Security Scenario
– Visual Dashboards
– Centralized Collection and Storage Of Logs
Solution Implementation Delivery Service Content
Consulting & Planning
Product Implementation
Security Operation Service
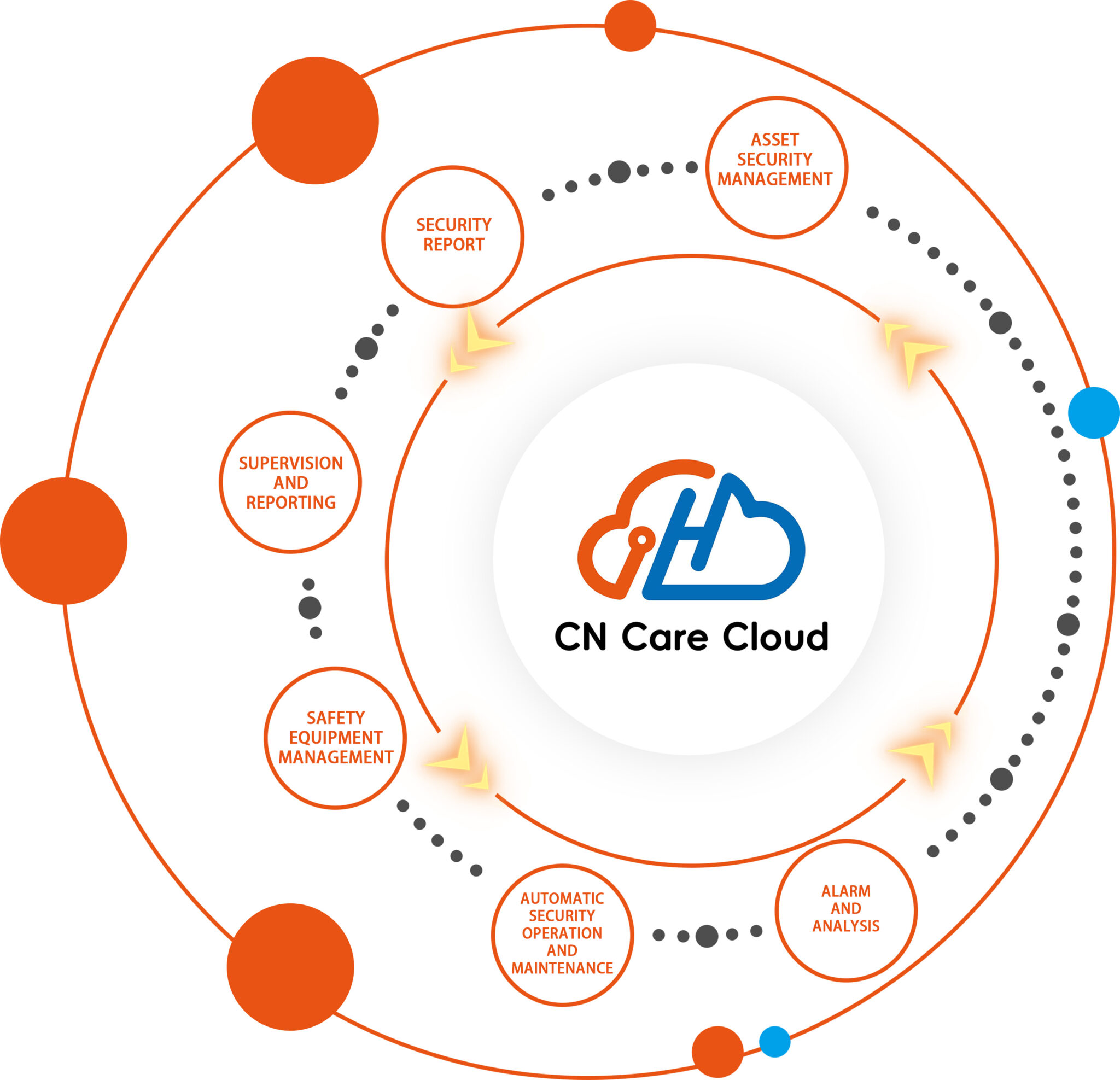
Security Service Architecture

Solution Implementation Delivery Service Content
Visual Dashboard
Flexible Deployment
Diversified Data Collection
Centralized Management
Safety Compliance

Integrate and Utilize Existing Resources To Protect Investments
Modular Functional Architecture, Easy to Deploy and Use
Support Multiple Cloud Environment Architectures
Rich Industry Security Operation Scenarios
Comprehensive regulatory targets
and management equipment
Enterprise Assets
– Network business
– IT equipment
– IP/domain name
– Information assets
– Intranet assets
– Internet exposure
– IT equipment
– IP/domain name
– Information assets
– Intranet assets
– Internet exposure
Service Components
– Application
– Database
– Middleware
– Database
– Middleware
System
– OS
– Container
– Virtualization and Cloud
– Container
– Virtualization and Cloud
Hardware Equipment
– Server
– Storage
– Network
– Security
– Storage
– Network
– Security
Data Center
– Computer room
– Cabinet
– Cabinet

Expanding your network horizons
Ready to Upgrade
Your Business Connectivity?
Contact us today for a consultation
and get a tailored quote for your enterprise broadband solution.
and get a tailored quote for your enterprise broadband solution.
(852) 2138 9398
Location
Hong Kong
Suite 3606, 36/F, No. 39 Wang Kwong Road,
Kowloon Bay, Kowloon
Kowloon Bay, Kowloon
Shen Zhen
10A21, Dongle Building, No. 2019-2 Shennan East Road,
Xinnan Community, Nanhu Street, Luohu District, Shenzhen
Xinnan Community, Nanhu Street, Luohu District, Shenzhen
Guang Zhou
Units 104-106, Block B, Guangzhou Venture Capital Town,
Haizhu District, Guangzhou City
Haizhu District, Guangzhou City
Zhu Hai
Rooms 1303-1305, 13th Floor, Windsor International Building,
2083 Jida Jiuzhou Avenue Middle, Xiangzhou District, Zhuhai City
2083 Jida Jiuzhou Avenue Middle, Xiangzhou District, Zhuhai City
Shang Hai
Room 312, Building F, Zhonghai Center,
No. 1256 Caoyang Road, Putuo District, Shanghai
No. 1256 Caoyang Road, Putuo District, Shanghai
