XDLP Data Security
By integrating user abnormal behavior analysis, intelligent recognition of sensitive data, and outsourcing full channel control capabilities, we aim to solve the data leakage risk faced by enterprises and establish a governance system for global data security and operation.
Customer issues/challenges
Remote work exacerbates the risk of data breaches
The circulation and leakage of core data assets of enterprises often occur in office scenarios.
Due to the impact of the epidemic, remote work has become the norm for enterprises, further exacerbating risks. According to the 2021 IBM data breach report, remote work has increased the average security protection cost for large-scale companies by $1 million.
Due to the impact of the epidemic, remote work has become the norm for enterprises, further exacerbating risks. According to the 2021 IBM data breach report, remote work has increased the average security protection cost for large-scale companies by $1 million.
Internal leakage is a major channel for data breaches
There are a large number of complex internal documents within the enterprise, and identifying and classifying sensitive data requires a lot of work. There are significant differences in best practices between different industries. On the basis of traditional IM chat tools such as USB and email outsourcing, SaaS applications such as cloud note taking and cloud storage bring new challenges to enterprises.
85% of data leakage incidents involve human factors
According to the Verizon 2021 Data Breach Investigation Report, 85% of data breaches involve human factors. How to intercept and block data leakage in a timely manner, while finding high-risk employees at the internal source of the enterprise and obtaining evidence in a timely manner, is the focus of enterprise data security construction.
CN Care – Pivot XDLP
Bulit-in rich sensitive data templates
Bulit-in 10 categories of sensitive data templates, supporting recognition of 111 rule types, and the ability to customize enterprise specific sensitive elements through machine learning.
Automated data mapping and identification of risk employees
Bulit-in data map, automatically scans the distribution of sensitive company data assets, allows for one-click search for the distribution of sensitive files, and supports one-click generation of employee level risk reports.
Support auditing and interception of nearly a hundred data channels
Supports data auditing for nearly 100 types of data channels, including IM channels, cloud storage, computer peripherals, email, and cloud notes. It also supports interception of IM communication and remote control channels.
Data outsourcing screenshot for verification
Support multi-channel screenshot evidence collection to record employees’ behavior when sending sensitive data in external files, for retrospective investigation of data leakage incidents.
Application scenarios
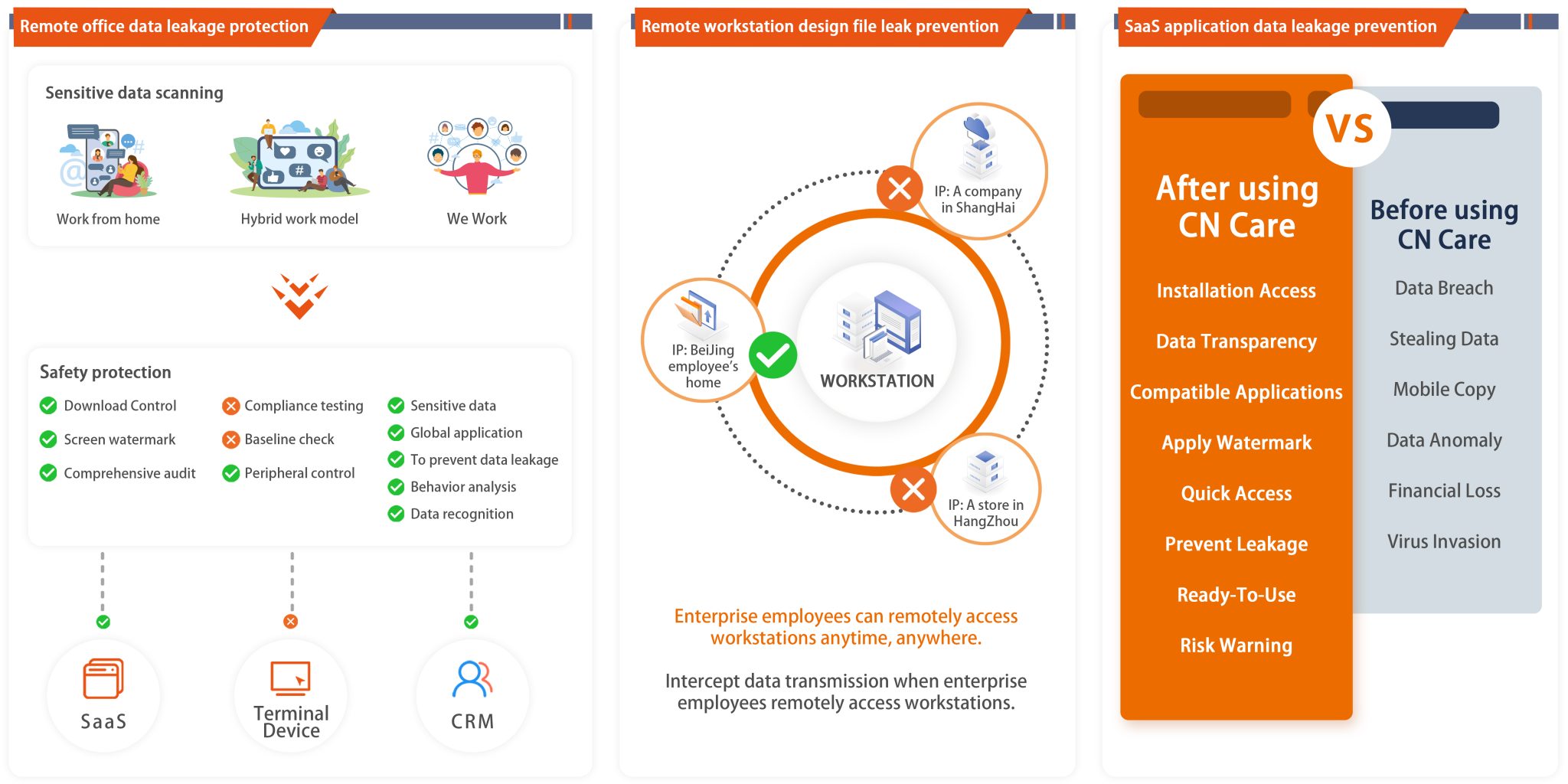
Product advantages
_XDR-Integrated-protection-loop-1024x1024.png)
Integrated
protection loop
protection loop
Integrating EDLP, NDLP, and UEBA, eliminating the need to deploy multiple products and reducing the workload of IT operations personnel
_XDR-Intelligent-classification-and-grading-1024x1024.png)
Intelligent classification
and grading
and grading
Intelligent recognition and automated classification and grading of sensitive data to help enterprises quickly identify and distinguish sensitive data within the enterprise
_XDR-Self-learning-of-enterprise-sensitive-data-1024x1024.png)
Self learning of enterprise sensitive data
Using machine learning and customizing sensitive elements unique to the enterprise
_XDR-Full-channel-blind-spot-control-1024x1024.png)
Full channel blind
spot control
spot control
The control channel supports a large number of channels, and controls sensitive data outsourcing across all channels efficiently and comprehensively
_XDR-Easy-traceability-and-evidence-collection-1024x1024.png)
Easy traceability and evidence collection
Employee sensitive data outsourcing records can be automatically captured and saved throughout the entire process before, during, and after outsourcing, making it easy to trace and retain evidence afterwards
_XDR-Automated-identification-of-risk-employees-1024x1024.png)
Automated identification of risk employees
Support one-click generation of employee dimension risk reports, and also enable one-click search for the distribution
of sensitive files
Expanding your network horizons
Ready to Upgrade
Your Business Connectivity?
Contact us today for a consultation
and get a tailored quote for your enterprise broadband solution.
and get a tailored quote for your enterprise broadband solution.
(852) 2138 9398
Location
Hong Kong
Suite 3606, 36/F, No. 39 Wang Kwong Road,
Kowloon Bay, Kowloon
Kowloon Bay, Kowloon
Shen Zhen
10A21, Dongle Building, No. 2019-2 Shennan East Road,
Xinnan Community, Nanhu Street, Luohu District, Shenzhen
Xinnan Community, Nanhu Street, Luohu District, Shenzhen
Guang Zhou
Units 104-106, Block B, Guangzhou Venture Capital Town,
Haizhu District, Guangzhou City
Haizhu District, Guangzhou City
Zhu Hai
Rooms 1303-1305, 13th Floor, Windsor International Building,
2083 Jida Jiuzhou Avenue Middle, Xiangzhou District, Zhuhai City
2083 Jida Jiuzhou Avenue Middle, Xiangzhou District, Zhuhai City
Shang Hai
Room 312, Building F, Zhonghai Center,
No. 1256 Caoyang Road, Putuo District, Shanghai
No. 1256 Caoyang Road, Putuo District, Shanghai
